Nıŋʝąƈąɬ 🐈 on Twitter: "Defender for Identity (MDI) Active Directory Federation Services sensor, protects the AD FS infrastructure and alert security teams to AD FS-based threats to defend hybrid identity configurations. Blog

Enabling Single Sign On into SAP using Microsoft proprietary Windows Kerberos authentication(GSS-API) | SAP Blogs

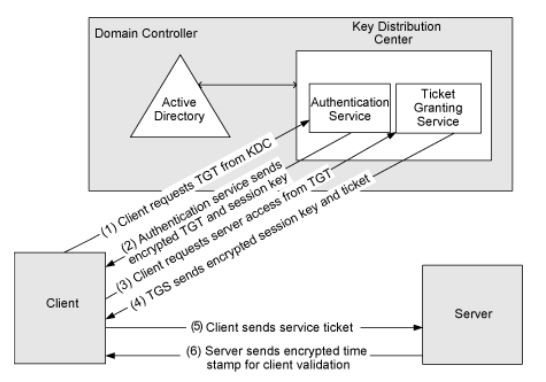
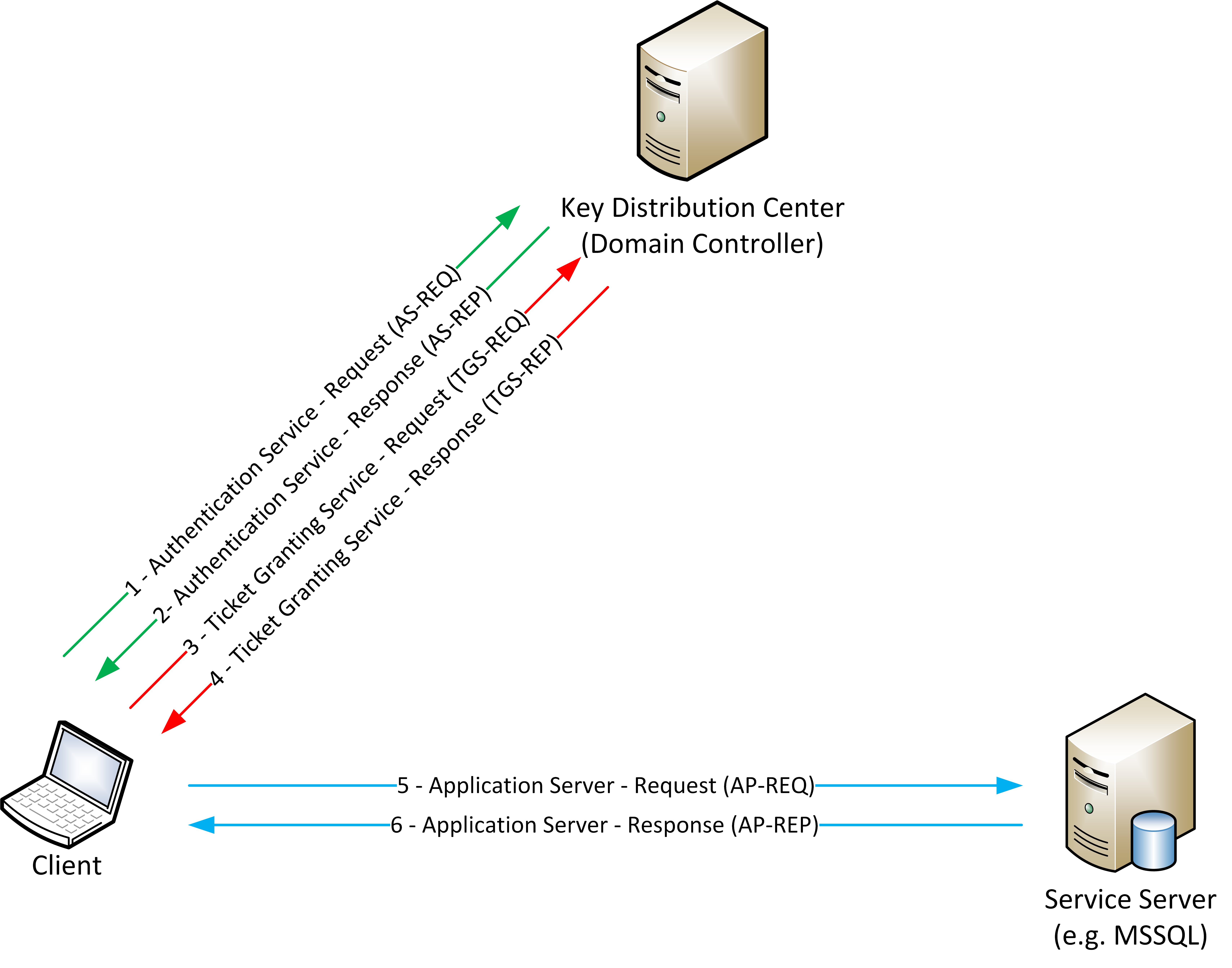
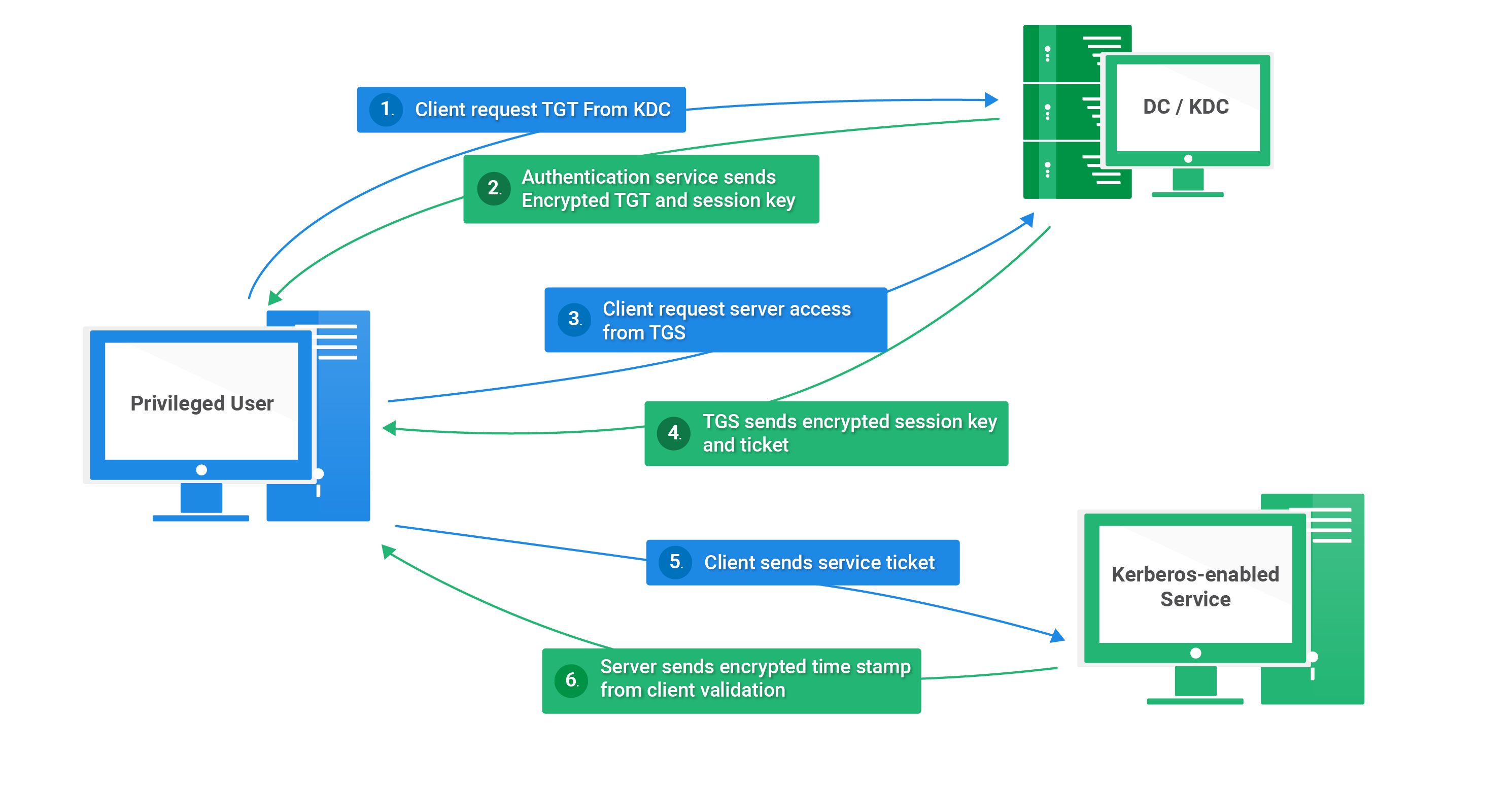
active directory Kerberoasting – Cyber Security Architect | Red/Blue Teaming | Exploit/Malware Analysis
Autenticazione composta e attestazioni di Active Directory Domain Services in Active Directory Federation Services | Microsoft Learn
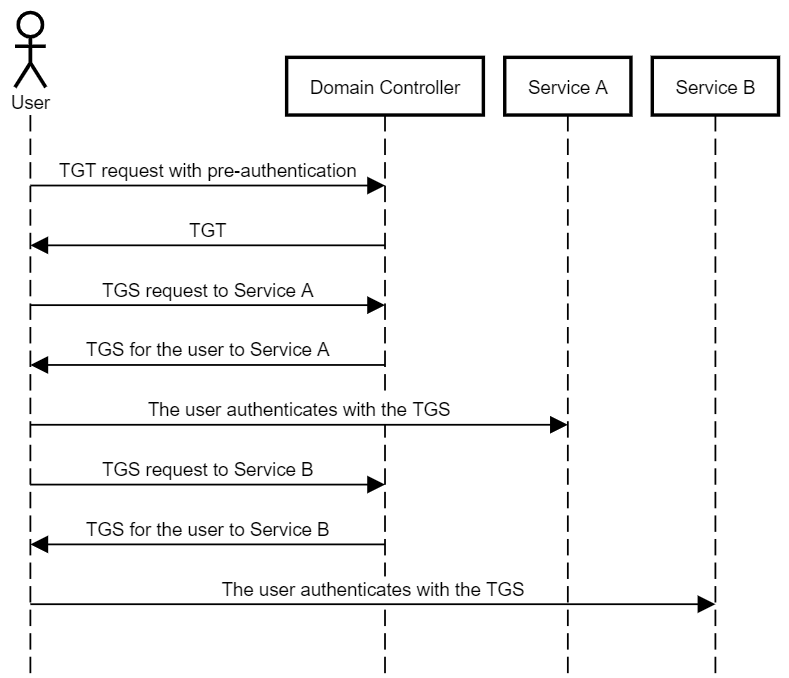
Wagging the Dog: Abusing Resource-Based Constrained Delegation to Attack Active Directory | Shenanigans Labs
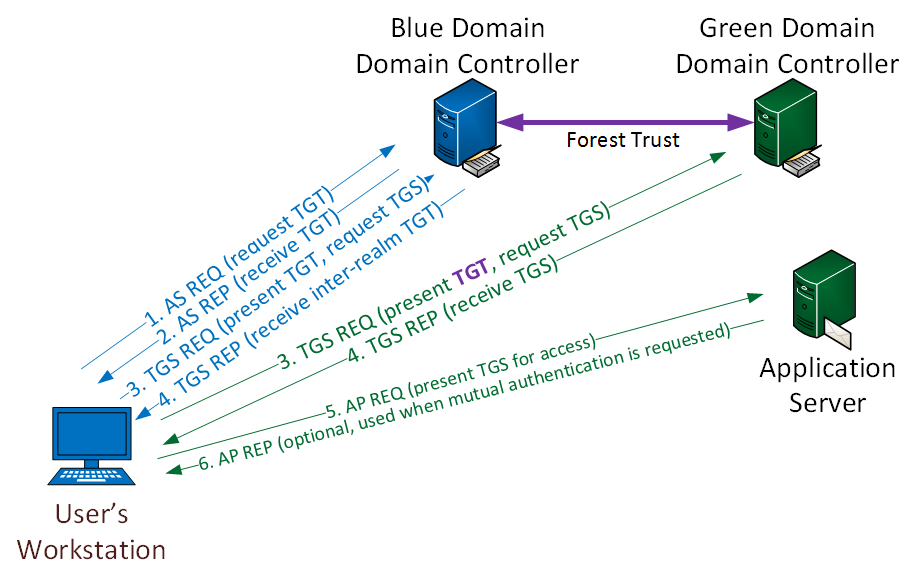
It's All About Trust – Forging Kerberos Trust Tickets to Spoof Access across Active Directory Trusts » Active Directory Security
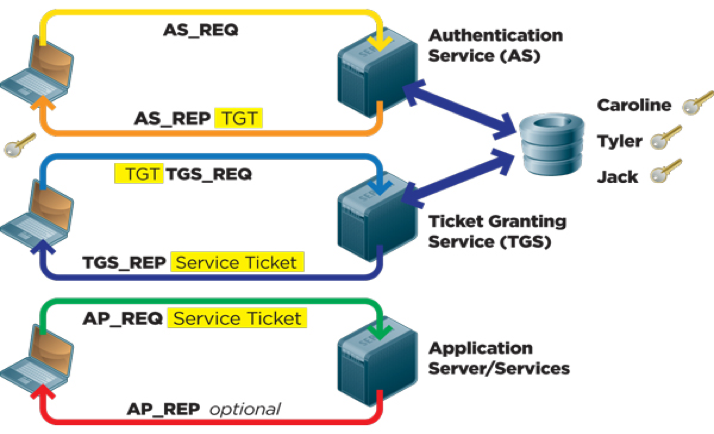
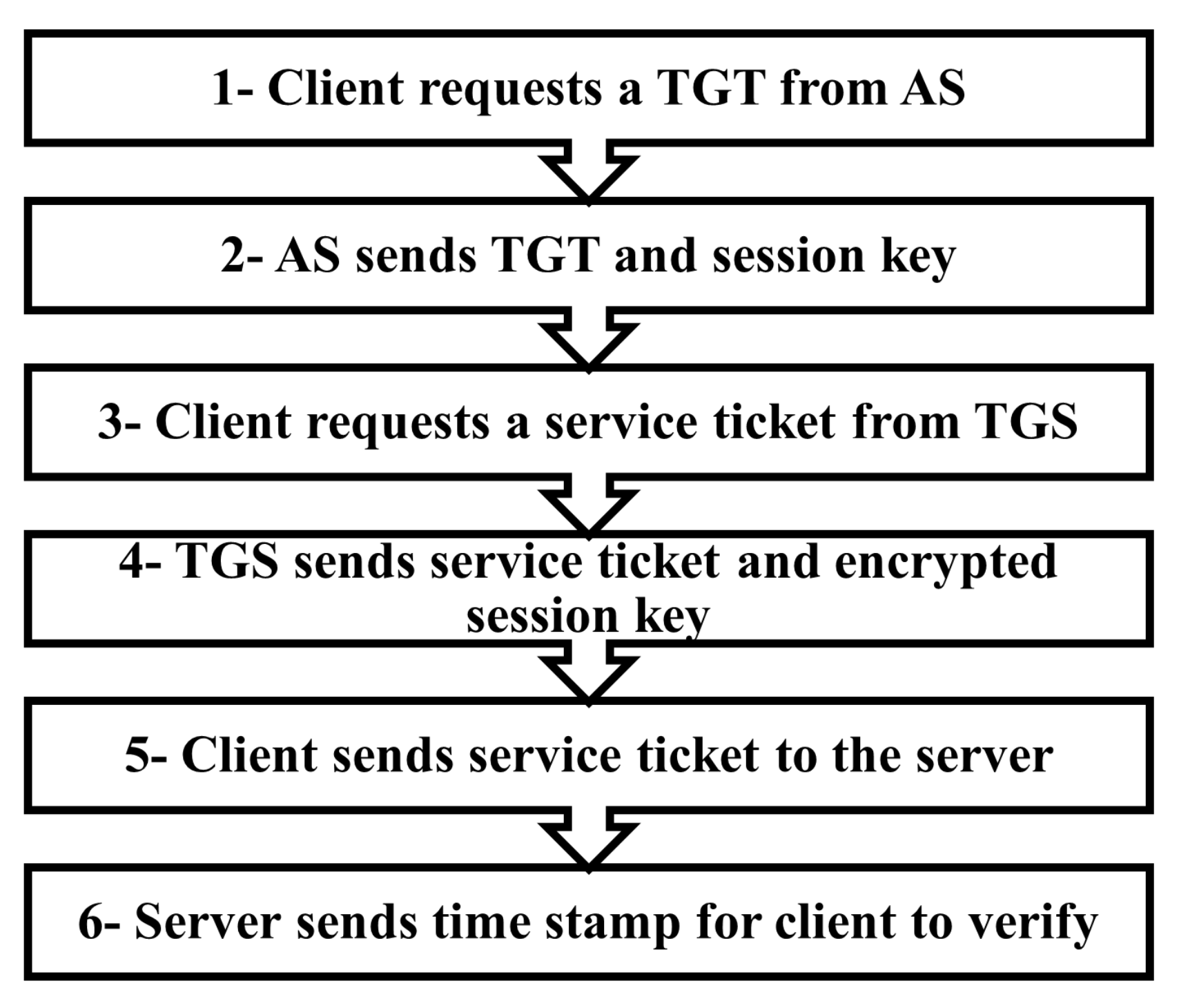

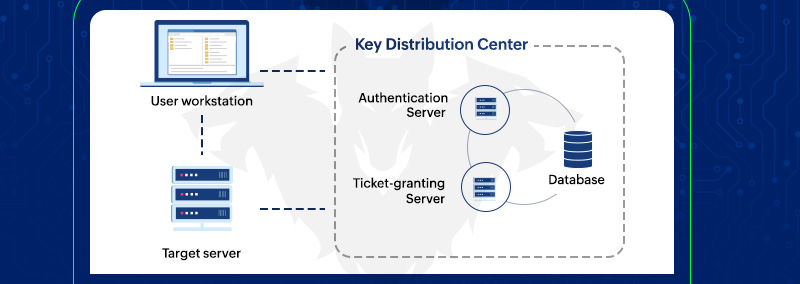
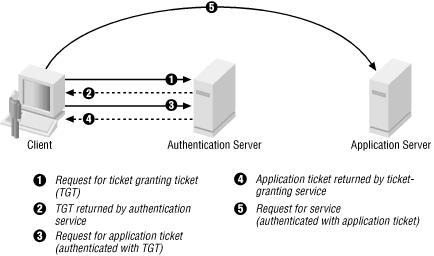
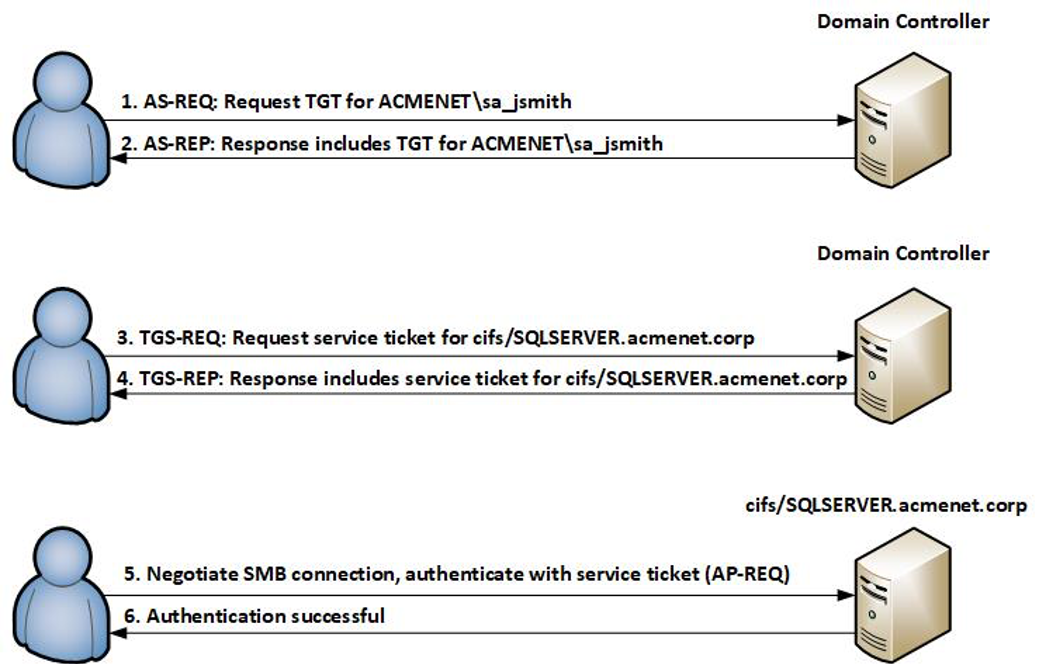




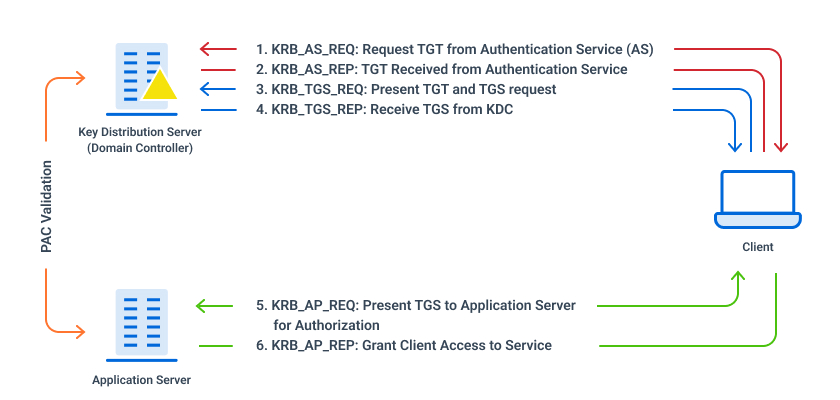
![Kerberos KRB_TGS_REP message [11] | Download Scientific Diagram Kerberos KRB_TGS_REP message [11] | Download Scientific Diagram](https://www.researchgate.net/publication/353593170/figure/fig5/AS:1051484670152706@1627704889837/Kerberos-KRB-TGS-REP-message-11.png)